Bitcoin Core’s ‘v26.0’ Upgrade Aims to Impede Eavesdropping, Tampering

[ad_1]

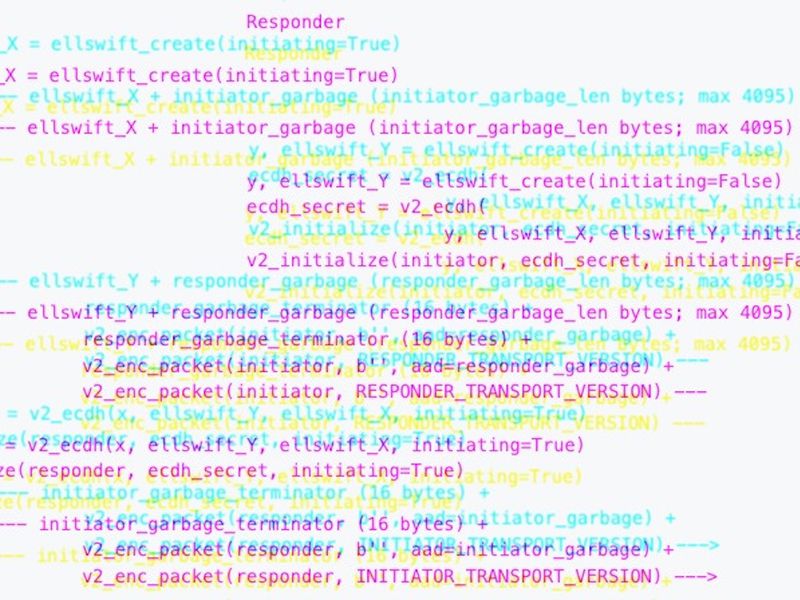
“This proposal for a new P2P protocol version (v2) aims to improve upon this by raising the costs for performing these attacks substantially, primarily through the use of unauthenticated, opportunistic transport encryption,” according to the proposal. A key benefit is that “encryption, even when it is unauthenticated and only used when both endpoints support v2, impedes eavesdropping by forcing the attacker to become active.”
[ad_2]
Source link
Recent Posts
Dear Diary, It’s Me, Jessica: Part 16
[ad_1] If you're new here, you may want to subscribe to my RSS feed. Thanks…
Google Faces Lawsuit After $5M in Crypto Stolen via Play Store App
[ad_1] A Florida woman, Maria Vaca, has sued Google in a California state court, alleging…
All About Water Purification: A Complete Tutorial
[ad_1] You may need to purify water to make it safe to drink. The process…
Protocol Village: Quai Releases Mainnet-Compatible Devnet, Crunch Lab Raises $3.5M
[ad_1] The latest in blockchain tech upgrades, funding announcements and deals. For the period of…
The Grim New Daily Life in Venezuela
[ad_1] If you're new here, you may want to subscribe to my RSS feed. Thanks…
World’s 3rd largest public pension fund buys $34M MicroStrategy shares
[ad_1] The third-largest public pension fund in the world has just bought nearly $34 million…
